本文将介绍如何较正确的在kubernetes下使用dashboard。
更换k8s-dashboard证书
生成证书
|
|
创建secret
|
|
创建k8s-dashboard
|
|
角色绑定
|
|
访问方式
-
使用kubectl proxy
kubectl proxy --address='0.0.0.0' --accept-hosts='^*$' -
NodePort,上面的证书是针对NodePort形式访问用到的。
1kubectl -n kube-system edit service kubernetes-dashboard将
type: ClusterIP改为type: NodePort,然后使用kubectl get service命令来查看自动生产的端口: -
API Server
如果Kubernetes API服务器是公开的,并可以从外部访问,那我们可以直接使用API Server的方式来访问,也是比较推荐的方式。
Dashboard的访问地址为:
https://<master-ip>:<apiserver-port>/api/v1/namespaces/kube-system/services/https:kubernetes-dashboard:/proxy/,但是返回的结果可能如下:1 2 3 4 5 6 7 8 9 10 11 12 13 14 15{ "kind": "Status", "apiVersion": "v1", "metadata": { }, "status": "Failure", "message": "services \"https:kubernetes-dashboard:\" is forbidden: User \"system:anonymous\" cannot get services/proxy in the namespace \"kube-system\"", "reason": "Forbidden", "details": { "name": "https:kubernetes-dashboard:", "kind": "services" }, "code": 403 }这是因为最新版的k8s默认启用了RBAC,并为未认证用户赋予了一个默认的身份:
anonymous。对于API Server来说,它是使用证书进行认证的,我们需要先创建一个证书:
1.首先找到
kubectl命令的配置文件,默认情况下为/etc/kubernetes/admin.conf,我们当前已经复制到了$HOME/.kube/config中。2.然后我们使用
client-certificate-data和client-key-data生成一个p12文件,可使用下列命令:1 2 3 4 5 6 7 8# 生成client-certificate-data grep 'client-certificate-data' ~/.kube/config | head -n 1 | awk '{print $2}' | base64 -d >> kubecfg.crt # 生成client-key-data grep 'client-key-data' ~/.kube/config | head -n 1 | awk '{print $2}' | base64 -d >> kubecfg.key # 生成p12 openssl pkcs12 -export -clcerts -inkey kubecfg.key -in kubecfg.crt -out kubecfg.p12 -name "kubernetes-client"3.最后导入上面生成的p12文件,重新打开浏览器即可,如下图:
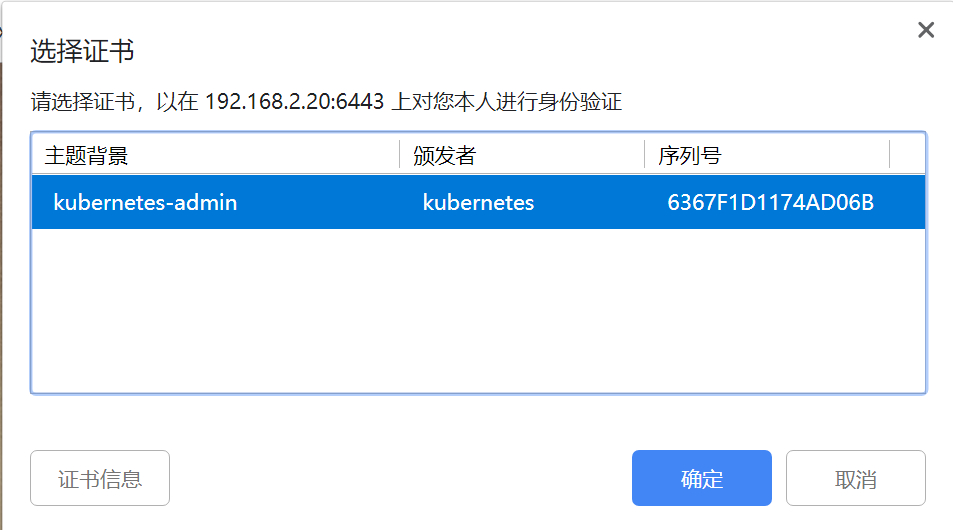
-
ingress
Ingress将开源的反向代理负载均衡器(如 Nginx、Apache、Haproxy等)与k8s进行集成,并可以动态的更新Nginx配置等,是比较灵活,更为推荐的暴露服务的方式,但也相对比较复杂,以后再来介绍。
获取token
获取之前binding的用户的token
kubectl describe secrets -n kube-system $(kubectl -n kube-system get secret | awk '/dashboard/{print $1}')
会话过期时间修改kubectl edit deployment -n kube-system kubernetes-dashboard
- args:
- --auto-generate-certificates
- --token-ttl=43200
参考地址:
https://github.com/kubernetes/dashboard/wiki/Certificate-management
https://github.com/kubernetes/dashboard/wiki/Installation#recommended-setup
https://www.cnblogs.com/RainingNight/p/deploying-k8s-dashboard-ui.html